
Has the constant noise of security alerts and news blasts about recent cyberattacks dulled - or sharpened - your sense of urgency to address gaps in your current data management system?
The reality is that you either fight with the rage of injustice or roll over and accept defeat. Will you give up all that you have built to cyber criminals? Of course not!
You will build an arsenal against those seeking to profit from your hard work.
Defend your Data
Are you relying on firewalls and public cloud security to protect your organization’s most valuable data assets? That is not enough.
Your top priority in building a comprehensive data and cybersecurity fortress is to use a top-rated data protection platform for Data Security Posture Management (DSPM) that actively secures data as it moves to/from your data repository and through your environment. Because multiple users must access data, the key is to use the principle of least privilege to ensure that data access is restricted to only what users need to complete their job. DSPM can integrate with your existing IT infrastructure and integrates with Extended Threat Detection and Response (xTDR) for a complete offensive and defensive cybersecurity strategy.
Depending on the size of your organization and your specific industry, data migration could be a high-risk, high-touch project because data security standards and compliance mandates still apply during migration. Many organizations outsource data migration and subsequent DSPM to a Solutions Provider experienced in data management.

If your goal in migrating to a multi-cloud architecture is to add speed, scalability, and efficiency to your current data capabilities, you must keep security as the top priority. Unsurprisingly, successful companies understand that data needs to be access-controlled, monitored, secured, and available—because executives use that data to make business decisions and growth projections—and to better serve their customers.
Protect Data with NIST Security Standards
According to the National Institute of Standards and Technology (NIST), data security “is the process of maintaining the confidentially, integrity, and availability of an organization’s data in a manner consistent with the organization’s risk strategy.” Data security is critical to developing cybersecurity maturity and protecting your entire IT infrastructure ecosystem.
Safeguarding your high-value data portfolio will also build brand trust with your vendors and customers – which can boost your brand reputation, fortify compliance requirements, and magnify your profits. Security experts encourage organizations to have a third party conduct a data risk assessment to discover existing people, processes, and technologies gaps. Following this review, organizations are advised to strongly consider DSPM to help secure their data repositories with the NIST pillars of cybersecurity.
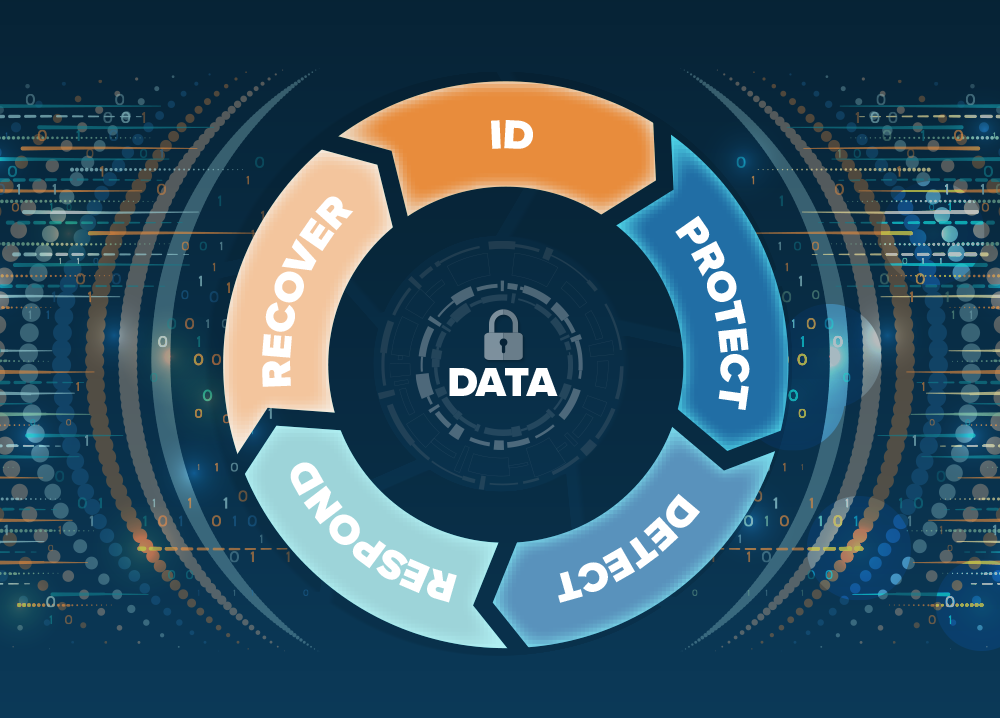
Does your organization consistently apply these NIST standards to secure your data and infrastructure?
-
Identify – run discovery for asset management, role-based permissions, data geographical locations, and vendor access.
-
Protect – maintain control of who and what is in your environment
-
Detect – a well-monitored IT environment is a safe environment. Automation and orchestration tools can quickly find behavior anomalies and alert for intervention
-
Respond – confine the blast radius of threats in your systems with clear remediation plans, communication trees, and investigation into root cause of infiltration
-
Recover – restore your data and environment and communicate delays to your employees and customers
Comprehensive Risk Management with DSPM
What’s the real risk of data compromise? Cybersecurity insurance may cover your compliance fines and remediation efforts. But the payout will not cover long-term costs associated with brand damage and employees losing confidence in a workplace that may have exposed their personal, sensitive data.
Kick dread to the curb and move forward with your growth plans—knowing that the right Solutions Provider can deliver stress-free Data Security Posture Management (DSPM) to mature and secure your data. With DSPM, you can uncover hidden and unstructured data sets deep within your data lake and bring them to the surface to categorize, prioritize, and ultimately tie the data to productivity.
As data lakes deepen and migrations to multi-cloud/hybrid environments are normalized, the risk of vulnerabilities going unnoticed becomes intolerable for a business’s risk profile. But you can stabilize your data with DSPM and secure your IT environment with a robust cybersecurity solution. A comprehensive cybersecurity solution compliments DSPM as it securely controls data through the entire data lifecycle—from creation to disposal—and across cloud and geographical boundaries.
Reach Security Maturity with TBC
TBC is a Solutions Provider headquartered in Scottsdale, AZ, with over 26 years of IT managed services experience specializing in cybersecurity, data protection, and infrastructure management. We partner with top-tier vendors to pair the best technology with our people and process expertise for IT service excellence.
TBC understands that demands on data verity and availability are high, and we can provide skilled technical implementation and best practice recommendations to organizations adding DPSM to their security detail. TBC is proud to partner with Symmetry Systems, one of Gartner’s “Cool Vendors,” to offer DPSM as the data security platform.
TBC offers DPSM licensure and continuous data maintenance and security monitoring, so you can rest easy knowing that our teams will be protecting your data assets. We often see clients with plenty of tools – but little oversight or integration – which creates more gaps and less efficiency. With our experience in data risk management and the right DPSM tools, we are confident that we will help build an arsenal to improve your data capacity, infrastructure performance, and cybersecurity programs.
.png)

