
Gartner is not alone in recommending consolidating cybersecurity services to take control of your security suite and eliminate the headache of managing multiple vendors. Many security experts are looking for ways to simplify their tech stack and improve their risk posture – and can do so with consolidation.
It is time-consuming and challenging to align multiple vendors to your business goals. Security and risk management leaders have the tough job of supporting business objectives and protecting customers and need support to realize the value of a consolidated cybersecurity platform.
Security leaders can build consumer confidence with a comprehensive security roadmap and convince end users by example - that they are reliable, focused on data safety & security, and can deliver on customer experience promises.
The Problem of Securing Infrastructure
Of course, you want the latest and greatest security tools and services to protect your business. However, layering many disparate solutions onto your existing toolset will only lead to broader security gaps and increase your vulnerabilities. The lack of integration is a primary concern for security managers, with 82% reporting that their existing tools missed security incidents.

With businesses using over 76 security tools to protect their network and infrastructure and still falling victim to cyberattacks, this is a solid argument to limit the complexity. By auditing and consolidating, you can lower costs by removing duplicative tools and services, eliminating unused licensing, and expanding infrastructure security with fewer vendors.
Misconfigurations and miscommunications are often blamed for security breaches – but the truth is that the lack of visibility is a significant risk.
Integrated Tools for Improved Security Posture
But you can revolutionize your security stack and regain control of your infrastructure if you contain sprawl, integrate tools, improve visibility, streamline operations, and mitigate risk by limiting your exposure from employing multiple cybersecurity vendors.
You see your peers adopting these acronym tools to bolster their cybersecurity posture:
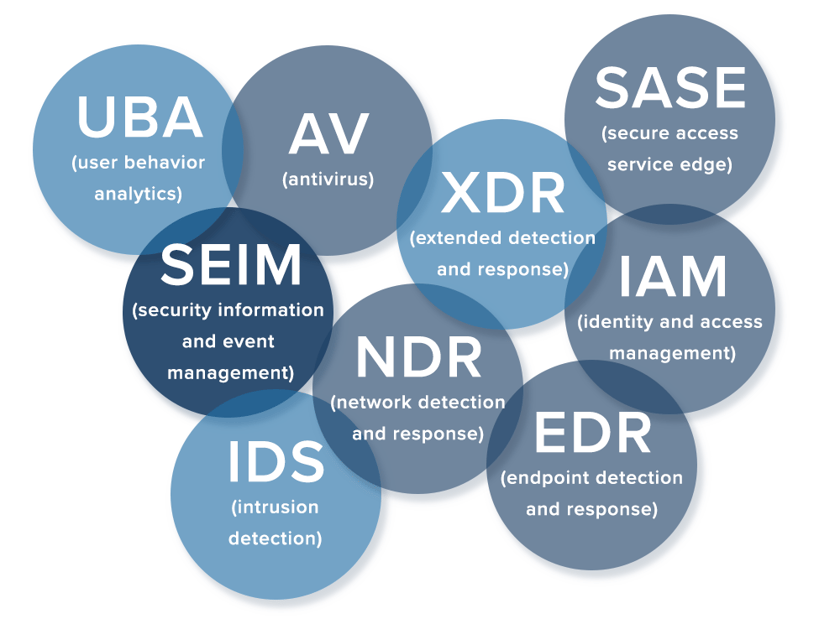
But what if you could consolidate all those acronyms into a single cybersecurity solution? Extended Threat Detection and Response (xTDR) is a single platform for unified security tools and, most importantly, for added infrastructure visibility.
The cloud-based xTDR solution improves your security posture by integrating multiple security tools that are easier to manage and meets NIST standards. xTDR masters the art of targeted response with the correlation and contextualization of threats. When data is gathered from multiple points and analyzed correctly, the data becomes actionable and can be integrated with security processes to improve alert fidelity and response.
xTDR is a consolidated security solution that brings together all the (above) acronym tools in concert with the following for better security, performance, and reliability of your infrastructure and network:
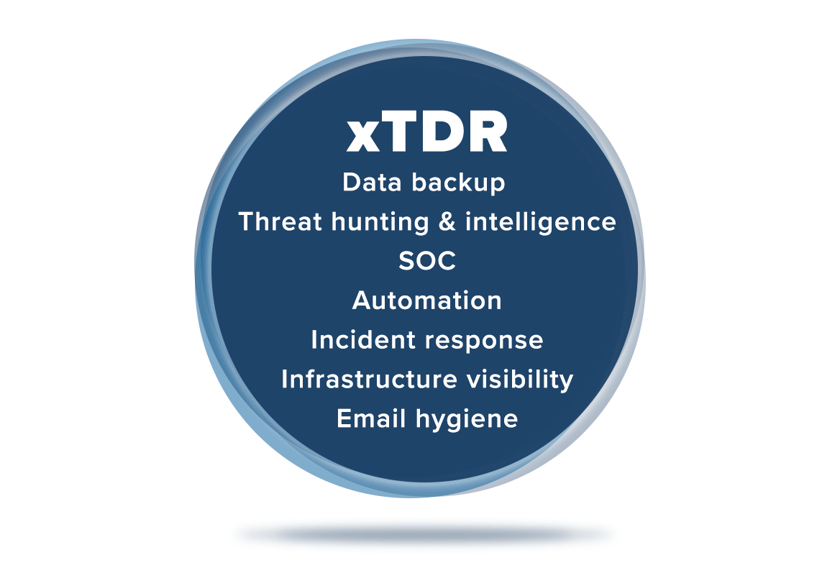
As cybersecurity risks rise and your security investments expand, it is easier to reduce conflict and delays by asking a few of your vendors to take on additional responsibilities or find a Solutions Provider who offers comprehensive IT security management.
Cybersecurity and Zero Trust
Many organizations focus their security efforts on firewalls and defending their perimeter – but fail to protect themselves from internal sabotage. As a business grows, so does the risk of negligent or intentionally volatile employees becoming threats to the organization.
So how does the Zero Trust Maturity Model help with cybersecurity? The model is used to build and implement a Zero Trust framework onto your IT environment to minimize risk with role-based access controls, continuous validation, and monitoring of lateral movement through the network.
In addition to Zero Trust, xTDR makes keeping tabs on internal users easier with behavior analytics tied to your active directory. Identity management will flag unusual behavior, file sharing or downloading, and access attempts for further investigation. Identity management is critical in a hybrid workforce and essential to a comprehensive cybersecurity program.
IT Solution Partnerships Unlock Value
TBC, an IT Solutions Provider with 27 years of experience as a managed security services provider, has launched its proprietary xTDR security solution to alleviate the complexity of managing multiple security tools and vendors.
A comprehensive cybersecurity program is mission-critical to protecting your whole-business ecosystem, and we strive to create a dynamic partnership with our clients to deliver the business outcomes they deserve.
TBC is a trusted provider of IT services and has resale agreements with many major tech vendors. We use those relationships to add value to our solutions and streamline everything from procurement to implementation to continuous management.
We know that businesses are concerned about investing time and financial resources. We understand the focus on time to change, time to value, time to resolution, and maximizing the IT spend.
Lean on the expertise of TBC’s IT architects and engineers to align your organization’s cybersecurity mission with quantifiable resources and continuous IT improvement.
.png)

