
How do you know you are getting the protection you paid for from your IT security tools? Extended Threat Detection and Response (xTDR) is a comprehensive security solution that offers both offensive and defensive methodologies to fortify and protect your digital infrastructure. Not only does xTDR demonstrate the ability to isolate and respond to threats and provides deep visibility and continuous monitoring as a layered defense to protect core business operations.
Keep it Simple, not Stupid
Simplifying your tech stack can eliminate duplicative tools and noise. Consolidating tech tools, solutions, and vendors will give you greater efficiency and visibility only if implemented and managed correctly. But it is best done intelligently.

|
Many organizations expect to achieve a stable and secure infrastructure because they spend money on multiple product purchases and vendor contracts. But more spending does not always equate to complete coverage of your IT infrastructure. The disconnect between product promises and how those products intersect with your edge creates vulnerability gaps in endpoints and makes it nearly impossible to respond adequately to threats.
Seek the advice of a trusted IT Solutions Provider experienced in security and endpoint management orchestration before you make any drastic changes to your tech stack.
xTDR for a Layered Defense
xTDR is a consolidated solution that will help you expand the reach of your various IT security, threat intelligence, analytics, and threat detection and response components. xTDR integrates disparate infrastructure and security tools to provide consistent visibility and meaningful analytics on a single platform.
Core xTDR functionality includes:
-
Network infrastructure protection
-
Access & Identity management
-
Remote/hybrid workforce security
-
Intelligent controls
-
Threat hunting
-
Process Automation
-
Operationalized threat intelligence
-
Improved threat response SLAs
-
Automation of resource-consuming, repetitive tasks
-
Cybersecurity preparedness
-
Advanced endpoint hygiene
-
Alert correlation
Business Value of xTDR
You can rest easy knowing the xTDR watchdog is actively limiting your exposure to threat actors. xTDR extends across your entire environment, creating a safe and reliable digital workspace, actionable data analytics, resolutions to vulnerabilities, and the protection of your network, endpoints, and cloud services.
Look at the graphic below to see how xTDR wraps security intelligence around business-enabling tools. With an ecosystem based on threat intelligence, integrated systems and tools, and SIEM automation supported by a knowledgeable and responsive SOC, xTDR can deliver comprehensive IT enterprise protection.
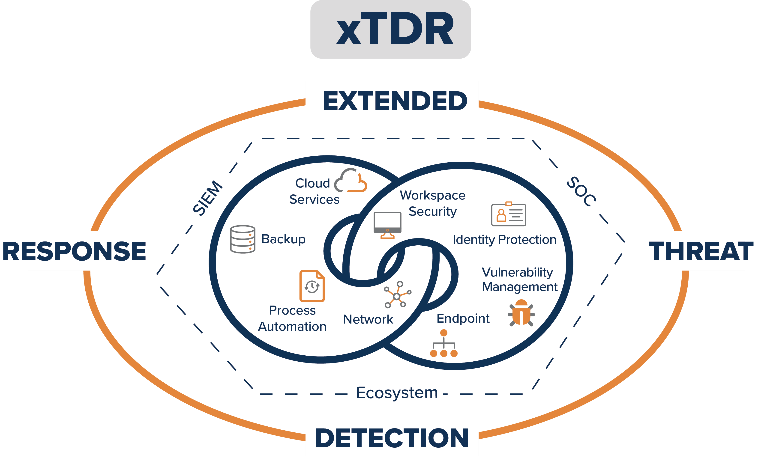
Security is data heavy. Software is feature heavy. Hardware is just heavy. Lighten your burden with xTDR’s contextualized data analytics, process automation, tool integration, feature consolidation, risk management, and functional management of your IT environment.
Organizations in growth phases will not be satisfied with the results of IT point solutions. Executives find that the quickest path to a stable IT infrastructure is to place the worry, burden, and responsibility of day-to-day operations on an IT Solutions Provider. Instead of employing more security staff and struggling to manually correlate data from various security tools, let someone else do the groundwork and give you the analytics you need to inform business decisions.
A properly implemented and managed xTDR solution should let you shift your focus to revenue-driving projects.
xTDR with TBC
TBC, an IT Solutions Provider headquartered in Scottsdale, Arizona, is proud to offer our xTDR solution. We think xTDR is a game changer in the IT security space.
If you aren’t confident in the performance of your IT security program, give us a call. If your IT health reports are not giving you the data analytics and actionable information you need to better protect your environment, let us show you one of our reports. Ask us for a demo if you aren’t already working from a single platform to manage your infrastructure security. If you have grown frustrated with the lack of communication from your current provider, reach out to TBC today.
.png)


