
Why are passwords no longer sufficient to secure user accounts? Because users tend to repeat passwords across accounts, choose easy-to-guess passwords, and even share passwords to get work done faster. And some people still insist on using passwords like "123456," "password," or "1234567890". Those take hackers less than one second to crack. The next step is Multi-Factor Authentication (MFA) and password managers to combat easily hacked passwords.
Although the days of changing your password every 90 days are gone (Yay!), corporations are relying heavily on password managers for access security. But even LastPass, a password management service, has been breached twice within six months. (Boo!) So how secure are your most valuable digital assets if you use a password manager or any other password management tool?
Security & risk management leaders must acknowledge that passwords are no longer a security asset.
What's better than Passwords?
Crime pays! Stolen credentials were responsible for 63% of hacking activities in 2022. Employees need to avoid oversharing sensitive information. The human element remains the weakest link in security interfaces, and passwordless authentication is an excellent way to reduce this vulnerability. But only if users are willing to take those extra security steps.
Passwordless authentication methods like FIDO2 keys or using biometric data (voice, retina, fingerprint), certificate-based authentication, location confirmation, and tokens/pins sent to mobile devices are some tools used to authenticate user identities for both mobile and desktop applications. But security comes at a price, and there needs to be more clarity about what constitutes a passwordless solution.
 |
Biometric authentication is expensive, and employees may hesitate to comply due to privacy concerns. One-time passwords (OTP) or two-factor authentications involve codes sent to mobile devices or emails. Both methods are time sensitive and cumbersome if many workload applications ask for an OTP for each login. Single sign-on technology is easy for users but risky because if those credentials are compromised, the hacker could access all the user's connected applications.
Identity and Access Management (IAM)
You know you need to go passwordless, but your authentication method depends entirely on your user base, the sensitivity of data and workloads, and the adoption rate of the tool(s) you plan to use.
Security & risk management leaders must not isolate Identity and Access Management (IAM) from their overarching security strategy. IAM is about controlling access to your network, core business processes, and data by knowing who is in your environment, how long they have been there, what they are doing, and if they are authorized to be there. Most organizations already have tools that could do some of these things but haven't maximized their use in IAM – or their security value.
Before leaping to passwordless authentication, security management leaders must create a strategy to define the source of truth for users' digital identities, find solutions that will not impede productivity, and align with stakeholders on implementing new authentication protocols across the organization. IAM leaders can use behavior analytics to remove passwords from the authentication process flow. Pinging in from the same location, same device, and same VPN every day is low-risk behavior. Add proof of identity steps when behavior or access location changes.
How to best enforce digital identities? Using the National Institute of Standards and Technology (NIST)'s Special Publication 800-63B Digital Identity Guidelines as a baseline for best authentication lifecycle management practices for authentication is a good start.
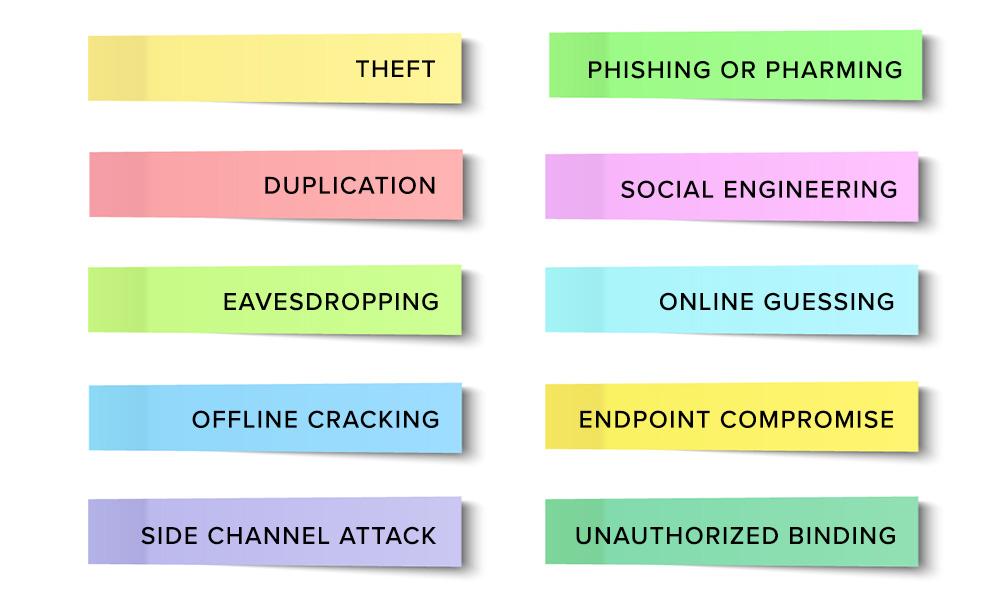
Take a look at the list below from NIST's Table 8-2, which offers organizations recommendations on how to mitigate against each of these common authenticator threats:
Cybersecurity Awareness Training
How do you get employees to buy into change? Through education and understanding. Only try to mandate passwordless authentication after warming up your audience with information, the reasons the changes will benefit them individually, and the importance of cybersecurity to the organization. Be aware that many people are uncomfortable using their personal cell phones to accept authentication keys. Don't discount those sensitivities--but feel free to use incentives to build adoption!
When you communicate the criticality of cybersecurity with transparency, you foster a culture of trust and shared responsibility across the organization. Invite employees at all levels to complete ongoing Security Education Training and Awareness (SETA) to keep everyone aware of the latest cybersecurity threats. Invest time in rolling out your passwordless authentication program and tie it to the need for perpetual cyber vigilance and personal accountability to secure digital assets.
In addition to education, periodically engage users with simulated phishing emails and track progress to share with the organization. Encourage your employees to accept ownership of their digital identity and learn how to protect it. In addition, IAM leaders should maintain rigorous offboarding standards to prevent sabotage, monitor user behavior on the network, and incorporate access management tools that limit access based on user role.
Invest in Whole-Business Security Controls
Securing your IT infrastructure takes more than a stack of tools. Security must be a whole-business endeavor. TBC, an IT Solutions Provider headquartered in Scottsdale, Arizona, is focused on helping organizations build a culture of security that permeates throughout organizations. TBC works closely with executive leadership, and IT teams to increase the efficiency and adoption of security tools and processes.
When you decide to prioritize your organizational security, TBC can help build security controls into your whole business, educate your workforce, and implement a passwordless authentication methodology that is secure, frictionless, and willingly adopted by your users. Our security teams will help you minimize your time-to-value by realigning your security strategy, tools, and processes to deepen your IT security and reduce risk across your organization.
.png)


